Sponsored by: Barkly - Make security something your users actually care about. Download the IT Pro's Guide to Raising Security Awareness.
![Here's everything that goes into a massive international speaking trip]()
International travel can look pretty glamorous from the outside and certainly it has its moments. But what many people don't tend to see (and indeed what's less interesting to share in 140 char tweets), is just how arduous it can be. So instead of just showing the good bits, I thought I'd jot down a bit more about just how much stuff I fit into one of these trips, my fifth (and last) big international one for 2016. If you think it's all fun and games or if you're just curious about what on earth it is I do, read on and do keep reading too because whilst it'll all start out looking nice, it'll inevitably have some very hard and probably very dark moments.
Here it is, all the good bits and all the bad bits captured candidly as they happen:
Day 1, Sunday October 2: Leaving home
A car picks me up from home just after 9am. Good time of day because I get to spend the morning with the family and don't have to start out at a crazy hour. One of the neat things about flying on Qantas business class tickets is a pickup and drop-off service which makes quite a difference. (Last year I wrote about how I justify more expensive seats and as you'll see, I maximise the space to do productive things.) It also means that right from the outset, I can actually get some work done:
![Here's everything that goes into a massive international speaking trip]()
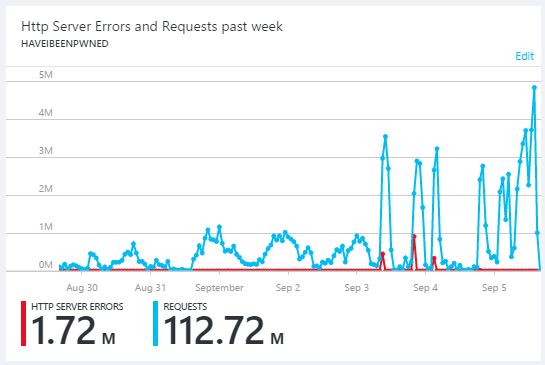
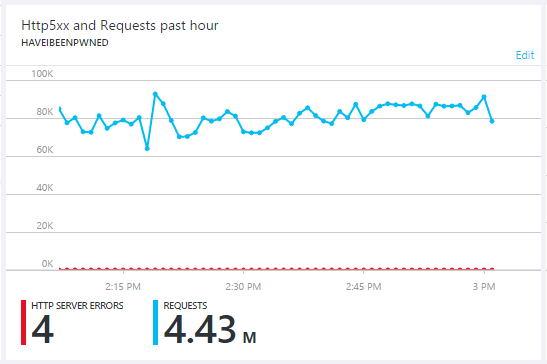
I get most of a new data breach loaded into Have I been pwned (HIBP) which is pretty good use of the time. I try and max out every spare moment of travel I get and an hour here with internet connectivity is pretty useful.
I take carry-n luggage only as it saves a heap of time at check ins and baggage claims not to mention all the walking I know I'll do with full kit in tow. I travel as light as possible, but "light" is a relative word:
And yes, everything in there I need either as a primary piece of equipment or as a backup. With all that and a carry-on bag for clothes, I can go from the car to sitting in the domestic lounge is 5 minutes tops. Domestic? Yeah, I have to fly from Brisbane to Sydney first so totally the wrong direction, but flights from Brisbane to Europe either weren't available on that day or were ridiculously expensive so here we are. I wrap the data load up in the lounge and jump on a domestic flight, flying back over home as I go:
![Here's everything that goes into a massive international speaking trip]()
It's a one-and-a-bit hour flight so I can't do much by the time I have some lunch too, but I get more done on another HIBP breach:
![Here's everything that goes into a massive international speaking trip]()
Get to Sydney and it's a bus to the international terminal then customs then another lounge. It's the last bit of wifi I'll get for a long time.
Onto the big plane and it's A380 all the way which is nice. First class is also nice, but let me explain - I fly business class because it means I can work, sleep and make way more productive use of the time - there's a clear ROI for me. Lots of business class travel gives me lots of points... points I can't do anything with. Seriously, I've even stopped trying because I've never been able to use Qantas frequent flyer points to book a business trip where I need to leave and arrive on specific days with a few months' notice at most. I've even tried to book the whole family to Vancouver and back on economy (which is just fine for a family holiday), and that's enormously restrictive too. Flexible on days a year in advance? Maybe, even some domestic flights I can use them on but other than that the only thing I've been able to do with the points is spend them on upgrades and even then, I'm accumulating them faster than I can spend them. I'll return from this trip with more than I left with courtesy of what I'll still earn from the business ticket.
On the way to Dubai I get a bunch of coding done for a feature someone was after for HIBP plus get through a module and a half of editing for my next Pluralsight course. I always try and record a course before travelling as editing is a really good use of flight time (no internet, I'm bored anyway and editing is tedious). I take both my Lenovo P50 (I can't begin to tell you how much I love this machine!) and my Lenovo Yoga 900 because I've never been able to get enough power from plane sockets to charge them so I burn through the battery on one then roll over to the other:
![Here's everything that goes into a massive international speaking trip]()
I'm really careful on international trips to plan sleep: I figure out when I need to sleep to ensure I can acclimatise immediately at the other end. I take it easy on the alcohol and have herbal tea and a lot of fruit. I get about 8 hours of restless sleep which frankly, is pretty good.
Day 2, Monday October 3: Dubai to London
I get to Dubai after midnight and attempt to fire up Freedome VPN:
Oh yeah, the whole we're-blocking-vpns-so-you-can't-use-voip thing. It was fine when I went through only a few months earlier, but now it's no VPN for me. That means there's no way I'm RDP'ing into any important services or connecting via SSMS to HIBP (and yes, they have encrypted transport layers anyway but they're way too valuable to risk). There are various other ways around this, but with only an hour on the ground there's not much point.
The shorter Dubai to London leg gives me enough time to edit another Pluralsight module so that's almost half of the 6-module course now done. I get another 2 and a half hours sleep then breeze through customs and baggage claim (another benefit of business travel with fast track tickets and only carry-on luggage). This is the ROI I speak of in paying for better seats: I've arrived rested and having been pretty productive, neither of which I can do with my 6'5" in frame in small seats.
Jump in a waiting car then struggle though London traffic as a strange orb normally foreign to the UK rises above the horizon:
I'm at the hotel by 9am and they let me check in early. I shower, then head straight out for the day. I've planned a massive walk and some stops to meet people because frankly, it's the best way of acclimatising quickly. Full on work starts the next day so the last thing I'm going to do is sleep at the wrong time for the new environment. Plus, it gives me a chance to head to Hamleys and buy my son something for his birthday, an event which I'll miss on this trip. I walk through the store with him on Facetime video and let him choose something that'll actually fit in my baggage (IMHO, a damn cool idea because Hamleys is awesome!)
Drone now in hand, I go for a walk to Hyde Park:
Then meet up with a company I've been talking to about various bits and pieces, have a coffee and a tour then some lunch. More walking, then coffee in the arvo with some Twitter contacts:
This is actually really cool doing impromptu stuff like this and meeting new people, something I really recommend if you're travelling somewhere new and have downtime. I'd been talking online with the Twitterers who came along and I've never had a bad experience catching up IRL with people like this.
By the time it's all done, I've had a good walk:
I eat at a normal time, go to bed just a little bit earlier than usual then sleep for 10 hours and get up at a normal time. This is invaluable - body clock is good! Anything remotely glamorous about travel ends tomorrow.
Day 3, Tuesday October 4: London workshop day 1
I'm up just after 6am for the first 2-day workshop of the trip (I'll do 5 in total). It's a repeat customer who I'd previously seen at another location in Jan and they liked it enough to run it again in London for other team members (I actually had to bring the whole trip forward a couple of days for this).
It's another rare sunny day in London:
And from here on in, it's pretty much business as usual which means a non-stop 8 hours of talking and running through the workshop:
I go for some beers with the attendees later on, get room service back at the hotel and then crash about 20:30.
Day 4, Wednesday October 5: London workshop day 2 and flying to Edinburgh
I'm starting a half hour early as I need to battle London commuters to get to the airport for a 20:00 flight. Frankly, this is about the most stressful parts of these trips - rushing from one event to another where I have to make a flight or the next thing gets jeopardised. I've not slept great either - fine until about midnight but then tossed and turned for another 6 hours.
Workshop runs fine though, clearly those at the event are having fun:
As much as we have a bunch of fun in these workshops, I'm really glad to see people getting practical knowledge they can use in productive ways afterwards. I put a lot of effort into striking the right balance between engagement, entertainment and education.
We wrap up and it's tube then the Heathrow Airport Express train then security then lounge. It's about as easy as it can be (carry-on bags folks - that's the secret!), and I use train time to catch up on emails. Lounge time is to invoice the customer and again, work through email backlogs - there's no downtime. I'm extra conscious on these trips that if I start to fall behind, it's really hard to get back on top of things.
It's a short flight but it's 20:00 by the time I get on it and I'm fading. I don't want to sleep though as that starts to mess with the body clock and I'm still acclimatising. I watch some Breaking Bad on the iPad (re-watch it, that is) and stay awake. I get a tram from the airport then walk down unfamiliar dark streets on my own while towing my luggage and watching Google maps:
![Here's everything that goes into a massive international speaking trip]()
This phase of travel - the one where I've had a really long day then flown somewhere and tried to get myself to a hotel late in the day - is the most mentally taxing. It's just lonely and it's as far removed as possible from my family and home in the sun. By the time I get to the hotel and into my room it's 22:30. I'm seriously tired.
Day 5, Thursday October 6: Edinburgh talk then driving to Glasgow
I wake on my own at about 06:30 after an awesome sleep and feel really good. I need to rehearse the talk I'm going to deliver that day (all my talks get rehearsed multiple times), so breakfast is quick as is the daily family chat. By the time I do all that plus check out plus get to the event it's 10:00 where I have a press commitment. And then another one. And then another one. And with a bit of socialising as well it's already time to set up for my talk, which ends up going perfectly to plan:
Per the earlier link, these only go to plan because I plan meticulously. I do some more press afterwards (seems to be a lot of these folks at the event) and then take a bit of a break. I try really hard to get out and about as well during these intense times; I have to get away from things sometimes and just step outside. And wow - outside was awesome:
But this is a perfect example of what I meant in the opening of this post: that's an epically cool shot that looks great in a tweet, but it doesn't show how damn tired I was by then nor how absolutely non-stop the preceding three days had been. This was snapped during one short break before heading back to the conference. But before I did that, I also record my 3rd weekly update video, my first away from home:
I get just enough time to edit and upload the video after my walk then it's a conference dinner. There's always people that want to talk and believe it or not (and trust me, I'm still getting used to this), people that want selfies with me:
I keep it early because there's then a 1 hour drive to Glasgow (although fortunately done by my gracious host), check in to the 3rd hotel of the trip already and then a 22:30-ish bed. Long day but hey, at least I got some exercise!
Day 6, Friday October 7: Glasgow workshop day 1
Crap sleep. Tossing and turning from midnight to 05:30 when I eventually got up and I'm not sure why, but it means starting a bit behind the 8 ball today. At least being up early means time to catch up on a bunch of things. It's another private workshop today and I walk the 20 minutes to the office and get there by 8am.
This is a Friday / Monday workshop and I need to make an early departure on Monday to catch a flight so we've crammed more into this session. That means 08:30 to 17:30 and everyone's brains are pretty much mush by the end of it, mine included. So, we get beers:
It's great having social interaction like this; you have a lot of banter that wouldn't normally happen in the more formal office environment and it's fantastic for building lasting relationships. I'm also always conscious that it's very easy to have a few too many beers and really set back my sleep and overall health in a pretty intense work period so I'm out of there by about 9.
Day 7, Saturday October 8: Down day in Speyside
The organiser of the workshop is taking me up to Speyside for the weekend so think picturesque Scottish scenery and whisky. Normally I'd be either flying somewhere or amusing myself on a weekend during a trip like this so it's quite unusual. We head off on a 3-hour drive and I start to see how Scotland is pretty cool;
Highways are boring though so I write a blog post about Chinese data breaches and get some more data loaded into HIBP. Without wanting to make it seem like I never tune out, when I come on a trip like this I'm considering it work from the moment I leave home to the moment I get back so whilst I definitely have some downtime later on, I'm not passing up this opportunity to do something productive.
Speaking of downtime, we find a cosy spot later:
Also, I learn that trolling Scottish people is like shooting fish in a barrel :)
Day 8, Sunday October 9: Heading back to Glasgow
My son is having his 7th birthday party today. It's hard being away at times like this, particularly seeing video of my entire family celebrating whilst I'm on the other side of the world. That's the nature of travel though and it's very hard to work it around personal events like birthdays.
I go for a walk to console myself:
Then it's back to Glasgow again which means more hours of highway and some time to work away on the laptop. Connectivity is a bit dodgy on my tethered iPhone so I'm crunching through tens of millions of records locally within SQL Server running on the Lenovo P50. Every time someone tells you "oh, you don't need a powerful laptop, you just spin up a VM in the cloud", remember that there's nothing like being able to run queries on the metal using a Xeon processor and 64GB of RAM sitting on your lap without and need for an internet connection. I get a lot of stuff done on that trip :)
I get back to Glasgow around lunch, check back into the same hotel I left the day before then go for a wander. I've lost my only toothbrush and the one pair of jeans I brought have got a hole in them so both those are on the cards for replacement (the joys of travelling light). These are the sorts of things someone like my wife would never screw up but somewhere within my compartmentalised mind I've put them in the "not really critical" box where all the things I can easily fix on the fly go. I do get to see some nice sights though:
I get back and do a few hours of work, including parsing some more data breaches for HIBP and editing some Pluralsight. I've had a 14km walk today so I reckon it's ok to pop open a bottle of the home brew my host gave me (which was sensational!) and splurge on a burger:
![Here's everything that goes into a massive international speaking trip]()
I crash out early again because the coming week has the busiest schedule of the entire trip.
Day 9, Monday October 10: Glasgow workshop day 2 and flying to Copenhagen
It all starts to get a bit "Groundhog Day" here - same routine over and over again. Get up, hotel breakfast, walk to an office somewhere and do my security thing. It all goes totally fine with this one finishing a bit early so I'm off at 15:30 and being driven back to the airport in Edinburgh. I'm flying Ryanair this time and people have set the bar of expectation very low but right up until getting onto the plane, nothing has gone other than perfectly smoothly:
And then I get to my seat... which is actually fine! Ok, it's not first class Qantas but it's right up the front on an aisle so even my long legs have plenty of room. I even wrap up a bit of cloud scaling after loading the Chinese NetEase data into HIBP:
I hit Copenhagen and get met at the airport by the workshop organiser and taken to the hotel. This is now the 6th time I've checked into a hotel already and it's only day 9. Fortunately, it is awesome:
![Here's everything that goes into a massive international speaking trip]()
There's a big lounge room, awesome bedroom, massive bathroom and big stone bath, then there's the rooftop; day bed, spa and a view over Copenhagen. I'm torn because on the one hand this is clearly awesome, yet on the other hand I'm there on my own without my wife, and there's going to be a very small number of hours where I'm actually awake in the place. Again, all this stuff can look epic in photos but the truth is frequently very different to the mental picture people frequently form.
Day 10, Tuesday October 11: Copenhagen workshop day 1 and .NET user group
It's the halfway point of the trip. It's also my son's birthday. And I'm not there. I have a good chat to him on Facetime, but it's hard being so far away:
![Here's everything that goes into a massive international speaking trip]()
I spent most of my teenage years living overseas away from everyone but my immediate family. Dad was a pilot which meant not just the half decade on the other side of the world as a family, but him frequently being away on birthdays or at Xmas or other times families traditionally spend together. But you make it work in other ways and I suspect that's shaped my tolerance for not always being with my family when I'd like to be. Other people would never be happy doing that and I totally get why.
I head up to my rooftop, first lamenting never getting to hop in the spa then snapping off a quick pic:
At breakfast to catch up on some backlog. It really is an awesome hotel; very Nordic yet somehow warm and cosy so I'm writing this by candlelight in the dark Danish morning:
![Here's everything that goes into a massive international speaking trip]()
More than anything though, I just appreciate having quiet time where I can do my own thing, even it's fleeting. I'm met at the hotel and then it's off to the workshop. Same deal as usual, same old spiel and fortunately, the same levels of enthusiasm from everyone. The day goes flawlessly and it's always great to see feedback like this:
I'm starting to feel run down though. Just a bit tired, a bit congested and feeling like I need some downtime. But that's not happening tonight, instead I'm doing a presentation to the local .NET user group:
The talk is the same one as I've just done in Edinburgh so at least preparation was simple. It's a user group in an auditorium within a university and it's a lot more casual than a formal talk you've got a limited time for so I embellish a bit. It goes for about an hour and then I spend another hour answering questions from the audience:
That goes great and I head back to the hotel with a few folks from the event when there's a suggestion of a local craft beer place. I'm tired, but I want to feel like I get to see at least a little bit of Copenhagen and spend some social time with people so two of us head out. The beer is rather sensational :)
Back at the hotel, I'm walking to the lift and the barman suggests I should really try some wine from a bottle he's just opened. I hesitate, then notice a sign which makes a lot of sense:
I don't know that I've ever just sat at a bar and talked to a bartender before, but he was a lovely bloke and we talked a lot about travel. Zero cyber-talk or what I was doing there and that was just fine as it was nice to tune out for a bit. I still got to bed around 22:30 which was ok and I got a great sleep in my awesome room.
Day 11, Wednesday October 12: Copenhagen workshop day 2 and flying back to London
First things first - check this out:
This was such an awesome little gift, particularly from the home of LEGO! Little things like that really make your day so I'm happy. The hotel also gives me a bunch of organic shampoos and things in a goody bag as they're a very alternative sort of setup here. Unfortunately, large bottles of liquids don't mix with carry-on baggage so the workshop organiser's wife has done quite well out of my stay.
The workshop runs fine and I leave 30 happy participants:
Train to the airport, breeze through security and definitely feeling tired by now. Fortunately, Copenhagen has an awesome airport with lots of good healthy food which was just what I needed:
When I checked in earlier I upgraded my ticket for a small fee (seems quite cheap if you do it late when there's spare seats), so I got to relax with a heap of room and eat a meal once I was on the plane. But that was the end of luxurious experiences for a while...
I train it into London from the airport via the Heathrow Express which is pretty awesome then wait at a lonely tube stop in Paddington:
![Here's everything that goes into a massive international speaking trip]()
This is the part of travel that starts to get depressing; late nights, tired from the day and strange - or no - faces. I don't think this train has been cleaned since the great depression either:
![Here's everything that goes into a massive international speaking trip]()
By the time I get out of the tube it's after 22:00. Problem is, I can't find the hotel. It was on the map and I'm in the right location, but all I find is a door in a nondescript wall. But there's an intercom so I buzz and am let in. I walk up a narrow, steep staircase into a tiny reception area and realise that yes, I'm in the right place. The receptionist explains that my room is downstairs... in the cafe. She leads me down and back out the front door then along a few meters to another locked door which is indeed a cafe. We walk past all the tables and chairs, past the kitchen and through a "private" door. I'm in room "C" which I suspect they named after "cramped". Or "cooped up". Possibly "can't believe this is the room", who knows.
I definitely don't expect a standard like I'd just come from in Copenhagen, but I was pretty unimpressed. There was no desk to work from, no window (there's a blind with frosted glass behind it), no phone and definitely no room service and as I later discover, no iron for the shirt I need to wear the next night.
I'm seriously missing home by now and frankly, I'm a bit over it all.
Day 12, Thursday October 13: London workshop day 1 and Pluralsight dinner
At least the room was quiet, other than the random buzzing that went off in the wall several times during the night, including at 05:30 which ended my sleep for good. I walk crookedly through the bathroom door, not due to the lack of sleep but because I'd hit my head on the low frame otherwise. Shower and grab an old fraying towel then have a quick chat to the family (they're beginning to feel less envious of my "glamorous" travel now).
Now here's the other problem: this workshop only has 6 people in it. There are various factors contributing to this which are all totally upstream of me and out of my control, but I'd normally have 5 times the number of people and unfortunately in this case, I'm paid based on profit share. Almost every other training event I do is a flat rate (those attached to conferences are the exception), which means that at least financially, attendance numbers have no impact on me. But this one will really bite and I'm as frustrated about the low turnout as I am about not using my time as efficiently as I could have.
But more importantly than that, 6 people have paid to come and see me talk for two days and above all else, they've gotta love this workshop. I still need to deliver the best possible experience to them and if there's one thing I never sacrifice on with work, it's quality.
Moving on, at least the coffee in the cafe-thoroughfare-to-my-bedroom is good and the workshop facilities are literally over the road. All 6 people show up too and despite the circumstances, I'm happy with how it's all gone. A couple of the attendees weren't very strong in terms of web programming ability (we do a bit of HTML and JS), so I pair people up which works really well. I must think about this more for the future; I first paired people in the US a few months ago during a private workshop where there were 50 people and I wanted to keep the number of machines down so I could spend more time with people. For all the same reasons pair programming works well, pairing in the workshop makes a lot of sense; collective problem-solving, learning from each other and the exercises run a lot faster too.
We finished at 17:00 and I'm chairing a dinner put on by Pluralsight at 18:00 for some CISOs and other security bods they have relationships with in London. I brought one shirt with me for this event but I can't iron it because, well, let's not get into all the things this hotel room doesn't have again. I walk 20 minutes to the event which fortunately, is in a nice spot:
![Here's everything that goes into a massive international speaking trip]()
Seeing friends from the company is really nice after the way I'd been feeling since arriving in London. It's always awesome seeing Pluralsight folks across the world whether they be staff or authors like me; there's a great comradery and for an event like this where I'm turning up to face enterprise customers, there's a sense of really being wanted. In fairness, workshops feel the same way too, but this is a welcome change from something that's rapidly becoming repetitive.
I finish up dinner and snap a pic of the hotel as I arrive "home", lit up in all its glory:
![Here's everything that goes into a massive international speaking trip]()
I enter through the locked cafe door hidden behind the stall in the foreground and enter the deserted cafe:
![Here's everything that goes into a massive international speaking trip]()
The door at the end of the hall leads to several rooms and I squeeze into mine, tired and a bit fed up. One week from now and I'll be on the plane home then shortly after, sitting in the sun in a place I love. I need to remember why I'm doing this, and having the life I have back home is a big part of it.
Day 13, Friday October 14: London workshop day 2
I wake to a message from my wife saying my son has hurt himself. There's a photo of his chin with a big split in it and blood everywhere. I call her but they're in the hospital and he's just about to get stitches so she can't talk. I check my email while I'm waiting for her and see a thread of problems relating to maintenance issues with the house that could have been pretty serious. It's made things really hard on my wife and now she's got an injured kid as well. This is the part of being away that really sucks and any remaining gloss that was on the idea of international travel is well any truly gone.
But these are all minor road bumps in the grander scheme of things and as much as they can distract you in the short term, you can't let them cause you to lose focus. Kids get hurt, stuff in the house breaks and so long as everything is fixable, let's move on and work on the things we can actually influence.
Back to day 2 of the workshop and it goes like clockwork. I do find myself embellishing a bit more as I do more of these and there's more news and other related stories to talk about. I'm spending a lot of time talking about Cloudflare in the HTTPS module I run not just because they do some very cool stuff in this space, but because their model raises many other interesting angles on the topic. For example, sites not protecting traffic back to their origin and being MitM'd (the Pirate Bay kerfuffle with Airtel in India is a great example), how we need to tackle the price and logistical barriers to going secure by default and who you should and should not trust to handle your traffic depending on your class of site (I question the logic of TPB using Cloudflare). I also talk a lot about defending against attacks by dynamically implementing firewall rules in Cloudflare when abuse is observed. If I'm honest, I'm a bit proud of myself with how well this model is working and people love seeing all the mechanics underneath the implementation. I'm happy to show and discuss things in a private setting like that I tend to keep out of the public eye too and it's very well-received, but does tend to eat into my schedule.
We wrap up and I head back to my hotel (just one more night...) then work on some HIBP features for a bit. Anywhere else and I'd be tempted to just order room service and chill out, but obviously, that can't happen here. Instead, I head out for a walk:
I grab some BBQ and wander around. It's pretty down near Tower Bridge and it was a good idea to get out regardless of the desire to escape the hotel. It also gave me a great spot to head back to the following morning; I haven't recorded my weekly update video and I really would like to keep them up. I've just gotta spend one more night in that hotel first...
Day 14, Saturday October 15: Leaving London and heading to Zurich
I'm up just after 06:00. I don't have to be, my flight isn't until midday, but the sooner I'm up then the sooner I'm out and I can focus on new things rather than lamenting the last couple of days. I head out with suitcase in tow and walk back to Tower Bridge (did I mention the importance of carry-on luggage already?). I'm there around sunrise and it looks sensational:
Now I know I post a lot of awesome Aussie sunrises, sunsets, sunny beaches and so on and so forth and I admit, I do enjoy the reactions to them (particularly from my UK friends), but surely this buys me back some kudos with the Brits, right?! It really is gorgeous and it makes an awesome backdrop for my fourth weekly update:
It's also a good spot to Facetime with the family so they get to see a bit of it. I think back to my teenage years overseas just before the internet and with no way of communicating with family short of very expensive phone calls or faxes (yes, faxes). Every time I'm away and I can actually look at my kids I think back to that and remember how fortunate we are to have the tech now, even though one of the kids looks a little banged up :)
Off to Heathrow, and I love this:
So simple, but just enormously effective. I find the first class British Airways lounge (a perk of having a ridiculous amount of travel on Qantas and partners) which is a pretty bloody welcome change of style from the last few nights. The flight itself has me right down the back but for less than 2 hours, I really don't care, I just zone out and watch some TV on the Yoga 900 (it's an awesome screen for this sort of thing, much bigger than the iPad and folds open like a tablet so you can use it on take-off and landing).
Into Zurich, train it to the city and definitely find myself in the right place:
The hotel is close... and it's fine. It's certainly not Copenhagen levels of fine, but it's a proper hotel and whilst it's a small room, I've got a desk and all the usual facilities you'd expect. I catch up on a few emails and other bits and pieces then head out for a walk. Zurich is nice:
![Here's everything that goes into a massive international speaking trip]()
I sit by the water for a bit and chill, but what I like even more than the visuals is the audio - there's a cacophony of very nice cars in this place! Ferraris, AMG Mercedes and a heap of high performance BMWs. Music to the ears!
I grab some dinner, but it's another lonely affair:
![Here's everything that goes into a massive international speaking trip]()
It's also expensive - spaghetti and a glass of wine is over $50 Australian which is kinda nuts. I walk back to the hotel before 19:00 and see two separate incidents of drunk English tourists getting into fisticuffs within 60 seconds of each other, both spilling claret on the cobbled Swiss streets. Nothing like a cultured European holiday...
I manage to rack up 15km or walking for the day which I'm happy with, but I should smash that tomorrow when I have a whole day off all to myself, the only one of the trip without having to be anywhere or travel to another location. Now that's luxury!
Day 15, Sunday October 16: Epic Zurich walking tour
Pro tip: if you want to sleep in, don't leave your alarm on. So yeah, up at 06:30 but it'd be highly unusual for me to sleep longer anyway so I'm not too upset. I spend a few hours attending to the usual electronic things, most of it while sitting in the hotel restaurant enjoying coffee and breakfast.
I head out just after 10:00 with a fog hanging over Zurich. I've got nothing more than a vague idea of where to go, but I head off and snap pics of anything interesting along the way:
It's going to be a big day distance wise, but it's also a day off and I want time to chill which means finding some nice sunny spots and just enjoying the place. I've got the Yoga 900 in my backpack too should I want to actually do something productive so I find a nice little spot to jot down some ideas:
And I did genuinely use that walking time to work on ideas too. I've had something in mind for HIBP for some time which I just haven't been able to properly position, but I reckon I've got it right now. I write it all down for later sanity checking and also manage to drag out an old blog post I've wanted to get out for a while and prepare this (I post Here's how I handle online abuse the following day). As much as I want to "tune out", I also like enjoying these quiet times to do the things I never seem to get around to while feeling rushed.
I eat in a nice little spot in the sun by the water then head back towards town to catch up with "someone from the internet". As with London, this is always a really nice way to meet local people and also as with London, it's a very positive experience and really adds to the trip. He takes me to a great local spot with a pretty epic view:
I head off for more walking, passing a pub with some rather tasty looking beers. I walk past... damn, they did look pretty tasty. Really tasty and I have had a lot of exercise today...
By the time I'm all done, I've covered over 25km which I reckon is a pretty good effort:
![Here's everything that goes into a massive international speaking trip]()
I've grabbed a salad along the way and a combination of lack of forethought and a relatively spartan hotel means eating it with my fingers. Such is my "exotic" jet-setting life.
Day 16, Monday October 17: Zurich workshop day 1
Back to work and the usual "breakfast with emails" routine. I'm met at the hotel at 08:00 and we wander out into the dark, misty Swiss morning. Train, setup at the office and then it's business as usual:
And it is usual - there's about 30 people in the room and we kick off the 5th and last workshop of the trip in tried and trusted fashion. Everything about the day went to routine which is just fine, but I find myself continually having to remember whether I've shown certain things already or made particular jokes or said other things which could easily have been said in a totally different workshop. Or this one. I'm not sure because I'm going through the same routine over and over again.
That night - cheese:
A bunch of people take me out for dinner very close the hotel (big tip from me - having events close to the hotel is awesome as I get to chill for a bit first), which is just a great night out. It's one of the most enjoyable evenings of the trip, just nice people and relaxed conversation.
They also had a much healthier gender diversity than most places. Still far from where we'd all like the industry to be, but well above par and it does make a positive impact on the views and perspectives that are shared not just at dinner, but throughout the workshop itself too.
Day 17, Tuesday October 18: Zurich workshop day 2 and train to Luzern
We're starting an hour earlier so I can get out earlier and head to the next event. I'm up at 05:45 and in the office setting up before 08:00:
Everything goes to plan, but by midday I'm tired. Really tired. I didn't have a late night or a lot to drink, but I'm conscious of how hard I've been pushing it for the last 2 and a half weeks. I don't feel so much run down or unwell, more that I'd just like to lay on my couch and watch movies for the afternoon. Clearly that's not going happen but I'm now pretty actively counting down the days and hours until I go home. In my mind, I've gotta get through until the end of tomorrow night when I'll be in London again, talk there then I'm done. I've still gotta get to Luzern later in the day and speak at an event there tomorrow, but that doesn't help my mind trick of convincing myself that I'm almost done!
Regardless, I power through the day with some help from a couple of strong espressos (don't make a habit of this folks, it's not good for you in the long run), and get out a couple of minutes before planned close at 16:00. Brisk walk to the train station and the 16:04 back to the city is approaching. I try to buy a ticket from the machine but the train is here so... I figure I'll talk myself out of it if a conductor turns up: "Crikey, I needed a bloom'n ticket? How many dollarydoos is that?". But no conductor so a free 11-minute ride is all mine.
Back at Zurich station, I catch up with Scott Helme. You may remember Scott from such episodes as "let's hack his car and turn on the heater while he's freezing his arse off in England and I'm chilling by the pool":
I'm conscious by now that I don't even know if I'm going to Luzern or Lucern. Or is it Luzerne? I'm literally at the point where I'm just following TripIt instructions and not worrying about the details. As such, I'm happy just to follow someone who's a bit clearer of mind.
It's nice catching up with a friend and being able to cut though the small talk. It's a one hour trip but it absolutely flies and we're off before we know it. We have a quick walk through what turns out to be a very picturesque little spot:
Check into the hotel, up to the room... and it stinks. It's really smoky and I honestly walk out and back in 3 times just to make sure I'm not imagining it and it isn't some weird Swiss air freshener or something. Nope, it genuinely stinks and while I'm here, what's with all the smoking in Europe? It's par for the course in a developing nation like China or Indonesia, but it always surprises me when I'm back in an otherwise very developed part of the world and people are puffing away, especially when you're sitting outdoors in a nice cafe and it's wafting over from the table next to you.
Anyway, unhappy reception phone call, back downstairs, new room. I have literally 5 minutes (maybe 6) before I need to meet up with Scott and head out for the Swiss Cyber Storm conference dinner.
It's a casual dinner for the event with lots of unfamiliar faces. Many events I go to are frequented by the same folks, both speakers and delegates, but it's all new here. Still, there were a bunch of really nice folks there:
And as with other stops along the way, there was the selfie:
Wandering home, I get a bit of a sense of just how pretty it is here:
Day 18, Wednesday October 19: Swiss Cyber Storm talk and flying back to London (again)
I've had a crap sleep. Really crap. Couldn't fall asleep in the first place so ended up popping the first sleeping tablet I'd had since arriving then woke up at 03:00 and tossed and turned until 05:00. I get up anyway as I'm meeting Scott for a 06:00 breakfast so we can head out and see a bit of Luzern before the event.
It's dark on our sightseeing tour, but it's also pretty awesome:
However, whilst walking around I talk to my wife. Son's stitches can't come out because he's having a reaction to the tape on his chin so the stitches have to stay in for a bit plus he's got conjunctivitis so now needs to be off school for the remainder of the week which means she's looking after him. It causes other complications as well, not least of which is her having to battle the traffic during the Gold Coast 600 which causes major delays around our house and she'll need to deal with it again tomorrow when the doc tries to take the little guy's stitches out again.
By the time I get to the conference centre where I'm speaking, it's finally getting light but I'm heading into a windowless auditorium. I get everything set up - on the stage, video perfect, audio perfect and the lot tested back to back over and over again. Everything is set to be perfect...
Then I get called on stage late. Then the video doesn't work. I'm standing in front of hundreds of people and only half my screen is visible. I'm mucking around with resolution and trying to make it all good whilst also trying to get the attention of the AV guys. There's nothing I can do but wait, so I'm making small talk with a darkened room of people that's more corporatey than my usual audience. Eventually though, it comes good and the show goes on:
It's quite a different audience to usual and I don't sense quite the same levels of engagement, but it might also be a more demure Swiss social norm. Regardless, from the feedback I do get (especially verbally afterwards), people are happy:
I get a chance to see John Matherly talk and for those who don't know him, John is the creator of Shodan, the search engine for the internet of things. Shodan often features in data breach and other related security stories as people discover all sorts of connected things that should never be there (MongoDBs with no authentication, for example). Scott and I catch up later with John and have a good chat; it's genuinely interesting work he's doing. The gears in Scott's head are obviously turning as he thinks of possibilities and this is one of the great things about events like this: exposure to other really smart people during casual conversation that gets you thinking about things in ways you never have before.
I'm out mid-afternoon, pick up bag, train station, airport, hang around for a couple of hours (finally get some more Pluralsight edited), on the plane and into London City Airport (so much better than battling Heathrow):
I grab a cab for the short ride to the hotel (I'm totally not up for working out trains by now), and then - for reasons beyond all logic - have a taxi driver that decides he can't take a credit card. FFS - you pick someone up from an international airport and then you can't take a payment with plastic?! It's such a minor thing in the grand scheme of life but the continued logistics of travel are really weighing on me. The hotel pays and bills me then I collapse into the tenth bed I've slept in since leaving home.
Then I realise that I really should run through this talk and get my timing down. It's a 15-minute version of the one I did in Edinburgh, Copenhagen and Lucerne which means a lot less slides and a very different pace. It's late, I'm tired, I've been going all day but I've just gotta do this one last thing...
Day 19, Thursday October 20: WIRED Security event and flying home
Up just after 5 but hey, it's the last day! I want to run through the talk again, catch the family, grab breakfast then get to the event by 07:45 where I'm having a breakfast catch-up with a bunch of people. Unfortunately, the laptop hasn't been on the charger (thank you dodgy international power supply adaptor), and I'm not sure when I'll get to add juice before tonight when I'll really need the power on the plane. But it's just one of those things that I need to put aside so that I can focus on the important issues of the day.
I get a drawing from my daughter while having breakfast:
![Here's everything that goes into a massive international speaking trip]()
It's been extremely hard being away, but I'm at a point now where I've made the mental switch to "I'm about to go home" so it doesn't pull at the heartstrings like it would have a few days ago.
I take a short 10-minute walk, leaving the last hotel of the journey and enjoying the last of the glorious British weather as I go:
I arrive at the event which is very slickly organised. Very well-dressed people here too, making even my best t-shirt look a bit casual. It's the financial district of London so I guess it's to be expected and frankly, by this stage of the journey, it doesn't bother me in the least.
So, the event turns out to be awesome. Not just very well-run, but a cast of really top-notch speakers with genuinely interesting things to share. People like Jamie Woodruff who had a great talk on social engineering (not theory, stuff he'd actually done), Moty Cristal who talked about negotiating ransoms demanded by adversaries who'd breached companies (the guy is an Israeli hostage negotiator - he's seen things!) and Mikko Hypponen who've I've spent a bit of time with in the past and really admire as a speaker.
Then there was Mustafa Al-Bassam, a quietly spoken bloke probably better known for the things he did as a member of the hacktivist group "LulzSec" a few years back than the positive things he's doing today. I had a chat with Mustafa after his talk and more than ever it struck me how so many smart kids find themselves at an infosec crossroad. He was only 16 when he and his cohorts were wreaking havoc and by any reasonable measure, deserved some serious repercussions as a result of their actions. Where the US in particular is throwing the book at people under the CFAA (listen to Lauri Love for a great example), Mustafa has faced penalties and moved on to become a smart, articulate and positive influence on infosec (he's presently undertaking a doctorate).
I do more interviews and then finally, there's my last formal commitment for the trip:
It goes flawlessly and there's a massive relief from having now made it all the way through with no mishaps. WIRED runs a really slick event and they have a full story on my talk published within a couple of hours, including a snippet of video from the talk:
I spend time talking to a heap of different people afterwards which frankly, is the real value proposition of these events. People. Connections. Discussions which would never happen online, at least not in the natural, organic way they do at face to face events. Plus, selfies:
This event has been absolutely spectacular; run with precision, fantastic talks, engaging conversation with delegates - I'm happy - this is the perfect ending to the trip. Come 18:15, it's time to play everything back in reverse from when I first arrived in London 2 and a half weeks ago, starting with the car:
![Here's everything that goes into a massive international speaking trip]()
The traffic is atrocious. It's going to take about an hour and a half to get to the airport but right now, I couldn't care less. I'm comfy and I'm not having to think. There's been a bomb in a tube station (or at least "a suspicious package") which has caused chaos that seems to be flowing over onto the road. The driver also seems to be having trouble seeing more than a couple of car lengths in front so he's on and off the gas like a crazy man.
Main thing is though that I'm at the airport with heaps of time to spare, fly through the check in and all the security bits and hit the lounge. There's massive relief to finally be done, but I'm ridiculously tired too. Take-off is about 22:30 and I'd normally be in bed by then at the best of times, let alone after the early start, long day and yeah, all the other stuff. I struggle to stay awake on the plane but I want to stay up long enough to eat. I sneak in one last weekly update video first though:
I kill a bit of time waiting for dinner, attempting to read some news via the in-flight wifi. Thing about wifi on these Emirates flights though is that there's barely enough of it to even send a tweet:
By the time I get to sleep, it's 01:something back in London. I think. Who knows, any sense of time is about be thrown out the window anyway.
Day 20, Friday October 21: Landing in Dubai and leaving for Brisbane
I don't know how much sleep I got on the near 7-hour flight, but when I was woken up a couple of hours before landing for breakfast I was in total sleep-deprived zombie mode. I honestly can't remember ever having woken up this tired before. It takes me a good 5 minutes just to be able to sit up and focus my eyes let alone actually feel like eating anything.
I'm into Dubai just after 08:00. The wifi is frequently pretty awful in the airport plus per my tweet on the way over, there's no VPN allowed. I want to get the weekly update video I mention above loaded so I chance it relying "merely" on YouTube and Ghost's SSL (which is there for precisely such occasions when you don't trust the connection anyway...)
I've got a couple of hours in the airport before the next flight which means catching up on things again. The easterly journey home is always tedious because of the two short nights you endure; it breaks your sleep and I find it much harder to recover. I read a good piece recently which explains the science behind why this direction is worse and whilst they talk about the longer circadian rhythms being the root cause (and I'm sure that's a part of it), the more disrupted sleep patterns is what really gets me.
Regardless, I get a bunch more Pluralsight editing done once I'm back on the plane until I'm having trouble staying awake again. By this time, it's starting to get dark and in an attempt to acclimatise myself to the changing time zones, I try to sleep. I'll take a melatonin tablet about an hour before attempting to sleep for the next few days which is meant to be a more natural alternative to full on sleeping tablets and helps get you back into a normal sleeping cycle (at least in theory). Probably a combination of that and how massively tired I was to begin with helps and I get maybe 6 hours.
Day 21, Saturday October 22: Arriving in Brisbane and then finally home
I awake with a start and I kid you not, I was having a dream about security. In fact, it was about someone breaching my own physical security at home and stealing digital content which is pretty much a nightmare in my books. But oddly, the dream was clear enough that it focused on very specific things I've been meaning to do for some time and I reckon if I'm now having nightmares about them, I probably should get onto that.
I get back into Pluralsight and almost manage to finish editing the entire course before touching down. I'm literally editing the last clip of the course (there are 30 in total), so I'm pretty happy that I've managed to fill all available "down time" with something productive.
As when I left home, Qantas provides a pickup service so I'm out quick and in a waiting car on the way home. Particularly after being away for so long, fast-tracking it home is awesome. It also gives me a chance to have my scheduled monthly meeting with my Pluralsight editor. I'm conscious this seems like I might be overdoing it to jump straight off a tiring flight into a meeting, but it's a commitment I like to keep and the timing is perfect given this latest course is as good as done. While I'm talking, my wife tweets me:
I've said it before in How I optimised my life to make my job redundant, but the support of your partner is critical for this sort of thing. I've seen the stress it can put on a relationship when your goals and expectations aren't aligned and it can be enormously destructive. I do what I do with the full support of a loving wife and we make decisions about travel like this together.
And then I'm home, far away from lonely airports and strange places, unfamiliar beds and cloudy skies. After seeing my family, the first thing I want to do is one of the simplest: sit down in the peace and quiet and have a good coffee:
Post mortem
Let me point out something that I already knew, yet it became all the more apparent in reading back through this: notice how I've only tweeted photos of awesome things but amongst these are private moments that were sometimes really pretty unpleasant. We all do this - share the positive things on social media - but I really want people to understand just how tough going it was in amongst all this.
I've stayed in 10 hotels and taken 10 flights consuming 54 hours of flight time (that's not including all the waiting time and transiting before airports). I've missed my son's birthday, not been there when he's been injured and left my wife to deal with the lot for 3 weeks. And here's another thing that came as a surprise to many people when I wrote about online abuse last week: I didn't get paid a cent for any of the conferences or user group talks. Yes, people pay to attend conferences and no, tech speakers rarely receive anything. In fact, if you look at the comments there you'll see that some don't even get their expenses paid.
There's one other important thing I elected not to record as I went because I didn't know if she'd want it shared publicly, but given she's blogged and tweeted it I can share it here:
Kylie has had to deal with chronic back pain since Jan when coincidentally, I was also away in the UK. For the fifth long trip this year, she's had to balance the pain with not just all the household duties every family deals with, but do it solo and whilst in pain. We still made the decisions for me to travel when I did with this in mind and looking back we wouldn't have made the decisions we did any differently, but her condition certainly added to the emotional strain on both of us and definitely added to the physical strain on her as well. I'm finalising this blog post two days after arriving home and I'm very happy (and massively relieved) to say that the operation she had this morning went perfectly. I'm now looking after the kids for the rest of the week while she recovers in hospital so there's definitely no laying around to get over the jet lag (I've been up since 03:00 this morning).
Having said everything about how tough it was being away, on the flip side of it all I've done well from the commercial workshops and that affords me more choices now that I'm back home. That'll mean regularly taking the kids to school and day-care, being there every time they play tennis and having lunch with Kylie each day. I suspect that many people would not willingly trade places with me given the family sacrifices involved, but this is a balance we have consciously decided is the right one for us.
I've now got a few months to do what I normally do from home which will mean more Pluralsight, working on HIBP, some local events and workshops and spending time writing about what I genuinely enjoy on this blog (I've a number of more technical pieces already in the works). Plus of course just generally looking after both Kylie during her recovery and myself whilst trying to get back into a more sustainable, healthy lifestyle, although I did actually manage to lose a kilogram whilst away despite the Swiss fondue (put it down to all that walking)!
I hope this has been an interesting read, I'm sure there will be those who both love and hate it for various reasons. If nothing else though, it's candid and honest and I hope it gives the reader some insight into what goes on behind the shiny travel tweets.
![]()